Lately we performed a scan on an internet portal using the website:
https://www.ssllabs.com/ssltest/analyze.html and must tell you the scan
was eye opening and Jaw dropping. Most important SSL 3.0 was supported and because
of this Poodle
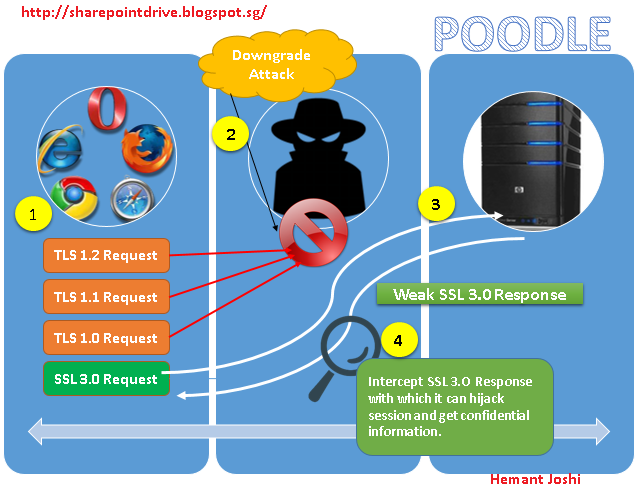
Let’s understand by the diagram above as to how it works on a high level
The key issue is the integrity of the padding on SSL 3.0 block ciphers. This padding is not verified by the protocol. This will allow an attacker to alter the final block of the SSL cipher if the hacker can successfully hijack the connection from an end user to the Web server.
There are a couple of caveats to the vulnerability; for the attack to work, the attacker must be on the same wireless network as you or in the path of your communications (as shown above), and your client must be running JavaScript.
This vulnerability in SSL 3.0 that can be exploited to steal certain confidential information, such as cookies. By exploiting this vulnerability, an attacker can gain access to things like passwords and cookies, enabling him to access a user’s private account data on a website.
Only if you rely on older browsers like IE 6 and others which still use SSL 3.0 then you have to think else I believe disabling SSL 3.0 altogether is a way to go.
So one backup plan involves preventing the "downgrade dance" that makes the Poodle attack possible. That patch, called TLS_FALLBACK_SCSV, basically forces the browser to inform the server when it offers a weaker security protocol, as it might during a "downgrade dance" attack. That allows the server to reject the connection. Unfortunately, the TLS_FALLBACK_SCSV workaround is only effective when both browsers and servers have been patched.
Please do check the coming article on: **COMING SOON** Windows Server Machine: How to disable SSL v3 Protocol

POODLE stands for (Padding Oracle On Downgraded Legacy Encryption), In this by using
a series of connection failures between a browser and website, an attacker can trigger
what is called a “downgrade dance” where the browser eventually falls back to using
the SSL 3.0 protocol to maintain communications. When this happens, the attacker
can use the exploit within SSL 3.0 to grab sensitive data.
Let’s understand by the diagram above as to how it works on a high level
- You use your browser to access a site and provide secure details believing TLS 1.2 is there to protect and your request is passing through it.
- Hacker does the downgrade or fallback on the earlier. That is, even if both the server and client support more modern protocols, as long as they're willing to support SSLv3, an active attacker can force them to use this old, terrible protocol. In many cases this fallback is transparent to the user.
- Now the request is send through the old SSL 3.0 protocol.
- Server respond by using the same SSL 3.0 which because of its flaws, the response can be intercepted and then attacker can hijack sessions and confidential information
The key issue is the integrity of the padding on SSL 3.0 block ciphers. This padding is not verified by the protocol. This will allow an attacker to alter the final block of the SSL cipher if the hacker can successfully hijack the connection from an end user to the Web server.
There are a couple of caveats to the vulnerability; for the attack to work, the attacker must be on the same wireless network as you or in the path of your communications (as shown above), and your client must be running JavaScript.
This vulnerability in SSL 3.0 that can be exploited to steal certain confidential information, such as cookies. By exploiting this vulnerability, an attacker can gain access to things like passwords and cookies, enabling him to access a user’s private account data on a website.
How to stop poodle attack
I have not seen till now any way to patch SSL 3.0 against the POODLE, but still
why to take risk when you can handle it by disabling SSL 3.0 altogether.Only if you rely on older browsers like IE 6 and others which still use SSL 3.0 then you have to think else I believe disabling SSL 3.0 altogether is a way to go.
So one backup plan involves preventing the "downgrade dance" that makes the Poodle attack possible. That patch, called TLS_FALLBACK_SCSV, basically forces the browser to inform the server when it offers a weaker security protocol, as it might during a "downgrade dance" attack. That allows the server to reject the connection. Unfortunately, the TLS_FALLBACK_SCSV workaround is only effective when both browsers and servers have been patched.
Please do check the coming article on: **COMING SOON** Windows Server Machine: How to disable SSL v3 Protocol

No comments:
Post a Comment